
Mobile technology has made it possible for people to do an amazing amount with tablets and smartphones within the workplace—including hacking the living daylights out of the corporate network and other people’s devices. Pwnie Express is preparing to release a tool that will do just that. Its Pwn Phone aims to help IT departments and security professionals quickly get a handle on how vulnerable their networks are in an instant. All someone needs to do is walk around the office with a smartphone.
Pwnie Express’ Kevin Reilly gave Ars a personal walk-through of the latest Pwn Phone, the second generation of the company’s mobile penetration testing platform. While the 2012 first-generation Pwn Phone was based on the Nokia N900 and its Maemo 5 Linux-based operating system, the new phone is based on LG Nexus 5 phone hardware. However, it doesn’t exactly use Google’s vanilla Android.
“What we’ve done is taken Android 4.4 Kit Kat and recompiled the kernel,” said Reilly. “On the backend, it runs our own derivative of Kali Linux, called Pwnix. Essentially it’s running a full-blown Debian OS on the back-end of Android.“
One of the benefits of the recompiled Android kernel is that the Pwn Phone can act as a USB host, just as PCs do. That makes it possible for the Pwn Phone to use external USB adaptors for Wi-Fi, Bluetooth, and Ethernet in addition to its built-in Wi-Fi and Bluetooth adapters. The external adapters for Wi-Fi and Bluetooth extend the Pwn Phone’s attack range and capabilities, and the Ethernet adaptor allows the device to jack straight into a facility’s local wired network for additional attacks.
The result is that the Pwn Phone can handle most of the functions of bulkier, less easily concealed security testing tools at a fraction of the weight—and with even less of the potential suspicion. This new generation of the Pwn Phone (and its larger cousin, the Pwn Pad) also makes it a whole lot easier for people without a great deal of penetration testing experience to quickly get up to speed and dig into potential vulnerabilities. Using the new Pwn devices can quickly convince you that it's important to turn Wi-Fi off on your phone when you’re in a public place.
The Pwn Phone comes with a total of 103 network monitoring and attack tools loaded, 26 of which have been configured for launch by touch from the device’s home screen. While all the tools run in a terminal window and have a character-based interface upon launch, some of the 26 touch-optimized tools require just one touch to execute. Others have been given menu-driven interfaces to reduce the amount of thumb-typing required to launch them effectively.
One of those “one-touch” penetration testing tools is EvilAP, a tool for creating a “malicious” Wi-Fi access point that can detect and respond to the Wi-Fi probe requests sent by devices as they look for previously used wireless access points. EvilAP can use the phone’s wireless broadband connection or another network to then pass through network requests while the phone’s user launches other attacks on the traffic. (These can include SSL Strip “man-in-the-middle” attacks against secure Web sessions.)
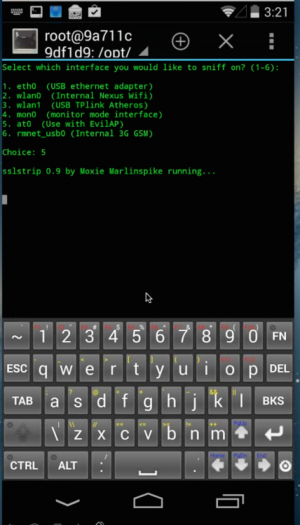
Other tools in the touch collection include: the network mapping tool Nmap; Strings Watch (a tool that watches for text within packets); the Tshark and Tcpdump packet analysis tools; the Metasploit and dSploit penetration testing toolkits; and the Kismet and Airodump wireless network monitoring tools.
Of course, if you’d rather not do any thumb typing at all while wandering around a targeted area for stealth purposes, a good portion of Pwn Phone's functionality can be controlled remotely. Just as with Pwnie Express’ other penetration hardware, the Pwn Phone can be configured using Web-based administration tools over one of the six covert channels provided in the phone’s toolset to connect through the network being tested or through its wireless broadband connection. And a remote terminal session to the phone can be opened via a reverse-SSH connection back to a PC. That means security surveys can be done without the Pwn Phone-carrying foot soldier ever pulling the phone out of his or her pocket. A remote security pro can even handle the whole show without leaving home.
Data collected by the tools—such as logs for packet captures from Tshark (the text-based version of the WireShark packet capture tool) and captured text from the Strings Watch packet monitoring tool—are stored in the phone’s 32 gigabytes of local storage. If you need to make all the data go away quickly, there’s a one-touch application that restores the phone to factory settings. It'll wipe away any sign that the phone might have been up to no good.
These are all capabilities that Pwnie Express already offers in a slightly larger form factor: the Pwn Pad 2014, based on Google’s Nexus 7 tablet and Android 4.2 (“Jelly Bean”). The only real difference between the Pwn Phone and the Pwn Pad is form factor and price. The Pwn Phone will sell for around $1,295, while the Pwn Pad is priced at $1,095. Of course, if you’d rather piece together your own Pwn Phone on an existing Nexus 5, there will eventually be a community version of the software available for download.





You must login or create an account to comment.